Community
Become part of Acurast’s vibrant community. There are many ways to engage, contribute and claim exclusive rewards.
Become part of Acurast’s vibrant community. There are many ways to engage, contribute and claim exclusive rewards.
Get to know Acurast. Explore our story, dive into the technical documentation, and see who we’re partnered up with in the ecosystem.
THE GAME CHANGER

THE DECENTRALIZED DISRUPTORS
Acurast leverages the security features of the smartphone to turn the device into an independent and completely locked compute unit, offering the highest level of security against bad actors with physical access. This enables verifiable hardware authenticity and secure processing of confidential workloads.
Smartphones are the most battle tested devices worldwide – billions rely on their security. With built-in Trusted Execution Environments (TEEs) and best in class Hardware Security Modules (HSMs), smartphones offer a higher level of security than servers ever can.

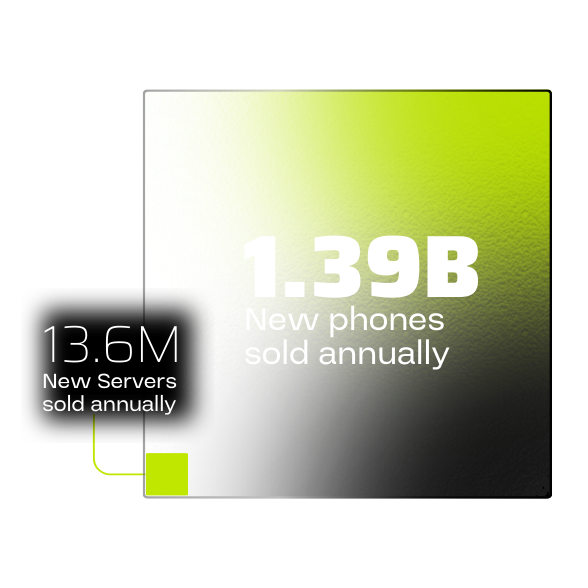
Acurast harnesses compute in billions of smartphones, the most distributed and refreshed computing hardware globally. With 1.39 billion smartphones sold annually and a 2.75-year replacement cycle, it enables a scale conventional servers can’t match.
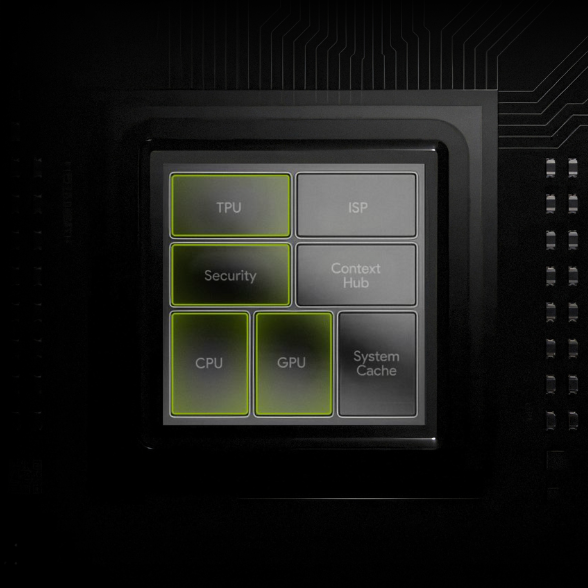
Acurast requires the security chip to create the official hardware certification – issued by the Original Equipment Manufacturer (OEM). This ensures verifiability through cryptographically proven attestations rather than unverifiable claims.

Acurast delivers confidential compute, allowing sensitive AI models, mission-critical data, and privacy-focused operations to be processed securely without risk of tampering or interception.
THE DECENTRALIZED DISRUPTORS
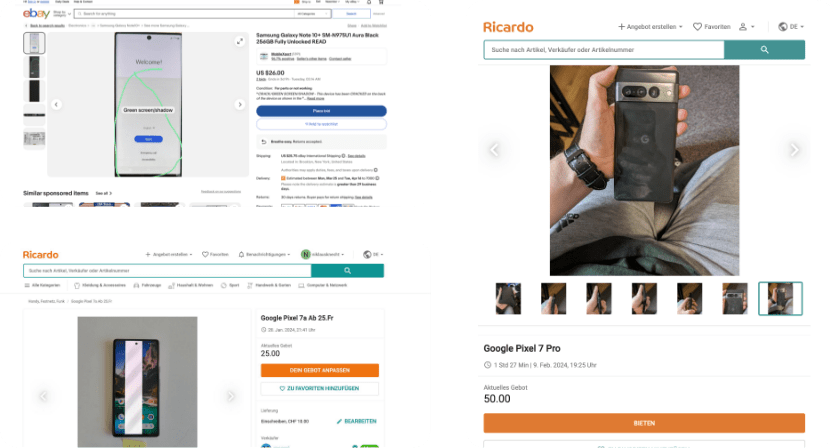
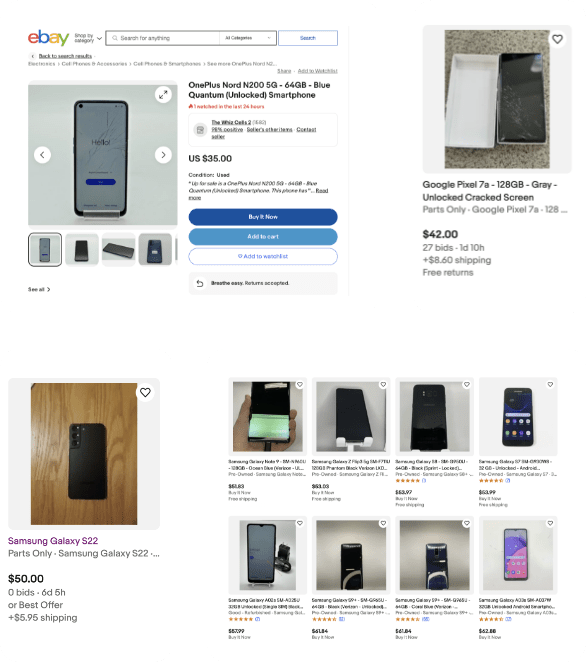
The second-hand market is filled with mobile devices with broken screens but fully intact processors, poised to transform into potent compute powerhouses on Acurast.
From a $2933 server to an upcycled Pixel of ~$25 on the second hand market.
DELL RACK SERVER
Price
$2’933
BY GOOGLE
Price
~$25 $499
Opportunity